I remember being back in college writing little trojans for windows and linux. Hardware trojans troubled one of my lecturers. He had been paranoid, for a great number of years, about the complexity of computer chips and during one such…
GL.IB.LY
Thoughts on security, computing, business and stuff!
Blog Archives
Paranoia deepens for security people as hardware trojans cloak
Tagged with: amd, computer security, doping, hardware trojan, intel, logic gate, microcode, NSA, processor, rng, transistor, trojan
Posted in Security
Posted in Security
Adding a malicious system call to the Linux kernel – Rootkit
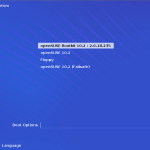
Introduction Today I am adding a malicious system call to the Linux kernel which will allow the caller to do something they cannot normally do in user mode. When attacking a Linux box our goal is usually to become root;…
Tagged with: computer security, kernel, linux, mssf, opensuse, rootkit, security, system call, virtual pc
Posted in Security
Posted in Security