Earlier today I got a massive SCORM object that contained lots of mp3 files. They were all high quality files, so I wanted to cut them down in size for web use. For this purpose I am using ffmpeg which you can…
Blog Archives
All configuration variables in Moodle code – Part two
Earlier we looked at how you can extract a list of all the $CFG variables in your Moodle code. Now that’s not of much use! We need to know where in the code all these variables hide. I feel some spooky awk a…
Posted in Computing, Stuff
Searching compressed Apache logs
From time to time things tend to go wrong and systems tend to go crazy. Sometimes these errors are more of nuisance than anything else, an intermittent annoyance you’d prefer not to investigate — trawling through logs is a pain in…
Rubber hose attacks!
Awesome! Hot linked from xkcd. Also, checkout wikipedia for more details on what the Russians do and how public key cryptography could get you killed or landed in jail (if you live in the uk).
Posted in archives, Stuff
Common translation errors in Moodle language packs
If you have ever had to deal with language packs you will know how much of a pain they can be. I regularly interact with 9 Moodle language packs and I don’t like doing that much. For some reason, can’t…
The command prompt has been disabled by your administrator?
I came across an old enough post on Didier’s blog about Group policies that have disabled cmd.exe from running. Didier mentions a few ways to get cmd.exe to run. The suggestion I like the most is to find the DisableCMD string in cmd.exe…
Posted in Stuff
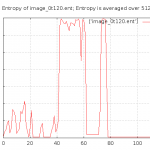
Analysing the byte entropy of a FAT formatted disk
Deleting specific emails from the postfix mail queue
A week ago a development database server lost power, which is usually no big deal only that I have some reporting scripts that run every 5 minutes for each database. When these databases became unavailable they (the scripts) like to…
All configuration variables in Moodle code?
Sometimes Moodle introduces some nice new configuration variables and I like to make sure that I know what they are and where they are. So to begin my investigation without heading off to the web I use the following command…
Posted in Uncategorized
Adding a malicious system call to the Linux kernel – Rootkit
Introduction Today I am adding a malicious system call to the Linux kernel which will allow the caller to do something they cannot normally do in user mode. When attacking a Linux box our goal is usually to become root;…
Posted in Security